Security has been always probably the most important thing a computing system must offer to its users. Through evolution of computing systems the principal or most important goal of the security is prevent misuse of computers.
Three fundamental pieces to security are:
- Authentication -- who user is
- Authorization -- who is allowed to do what
- Enforcement -- make sure people do only what they are supposed to do
For Authentication we use passwords, which are "secrets" between two parties, your computer and you with a password the machine can assume that it's me who are in the controls.
The system keep always a copy of this "secrets" but what could happen if a malicious user gains access to that list of passwords?
A possible solution to this problem is encryption - transformation that is difficult to reverse without the right key.
There are two roles for encryption:
a. Authentication.
b. Secrecy -- I don't want anyone to know this data.
Private key encryption
Private key: use an encryption algorithm that can be easily reversed, given the correct
key and hard to reverse without the key.
As long as password stays secret, get both secrecy and authentication.
But how do you get shared secret in both places?
Server keeps list of passwords, provides a way for two parties, A,B to talk to one another, as long as they trust server.
Notation:
"Kxy" is a key for talking between "x" and "y".
(text)"^K" means, encrypt message (text) with key "K".
//A asks server for key
A -> S ("Hi! I'd like a key for A,B")
//Server gives back special "session" key encrypted in B's key:
S -> A(Use Kab ("This is A!" Use Kab)^Ksb)^Ksa
//A gives B the ticket:
A -> B("This is A!" Use Kab)^Ksb
Public key encryption
Public key encryption is an alternative to private key: separates authentication from secrecy.
Each key is a pair: K-public, K-private
With private key system:
(text)^K = ciphertext
(ciphertect)^K = text
With public key system:
(text)^K-public = ciphertext
(ciphertext)^K-private = text
and:
(text)^K-private = ciphertext'
(ciphertext')^K-public = text
and:
(ciphertext)^K-public != text
(ciphertext')^K-private != text
and: cant' derive K-public from K-private or vice versa.
The idea is
/*K-private kept secret.
K-public put in a public directory.*/
For example:
("I'm tom!") ^ K-private
//Everyone can read it, but only I can send it (authentication)
("Hi!") ^ K-public
//Anyone can send it, but only the target can read it (secrecy)
In other words
(("I'm tom!")^K-private "Hi!")^K-public
//Only I can send it, only you can read it.
Some symmetric-key algorithms:
- DES
- 3DES
- AES
- IDEA
- SEAL
- RC4
- RC6
- Blowfish
Some asymmetric or public-kay algorithms:
- RSA
- Diffie-Hellman
- ElGamal
- Elliptic curves
For example purposes we made an implementation in python of the RC4 algorithm, one of the most used encrypt algorithms in protocols like:
TLS/SSL, WEP y WPA.
This algorithm uses a vector with 256 numbers and is divided in two parts, first part mix the numbers of the vector using a key as roth creating an intermedium key of
256 numbers; second part uses the vector to encrypt data mixing and interchanging the numbers.
#! usr/bin/python
class RC4:
def __init__(self:(
print 'RC4'
self.S=[]
def ksa(self, llave:(
self.S = range(256) # crea un vector de 256 numeros
j=0
for i in range(0,256:(
# Escoje dos números para mezclarlos usando los números de
# la llave como semilla. En este caso los caracteres de la
# llave se convierten en un numero entero usando ascci.
j = ( j + ord(llave[ i % len(llave)]) + self.S[i] ) % 256
(self.S[i], self.S[j] ) = ( self.S[j], self.S[i] )
def prga(self, texto:(
temp = ""
j = 0
for i in range(len(texto):(
# Utiliza la llave de 256 numeros para crifrar el texto.
j = (j + self.S[i+1]) % 256
(self.S[i+1], self.S[j] ) = ( self.S[j], self.S[i+1])
# La variable temp se usa para guardar el resultado del
# crifrado y convertir el número a hexagesimal
temp = temp + hex(self.S[(self.S[i+1] + self.S[j])%256]^ord(texto[i])).split('x')[1]
print "%s -> %s"%(texto, temp)
rca = RC4()
rca.ksa("LLave")
print "key -> LLave"
rca.prga("Este texto es muy importante")
The result of encrypt "Este texto es muy importante" unsing "Llave" as key is:
Firewall
[image obtained from: "http://www.itconsultingcrew.com/wp-content/uploads/2010/08/firewall.gif"]
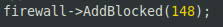
A firewall is a secure and trusted machine that sits between a private network and a public network. The firewall machine is configured with a set of rules that determine which network traffic will be allowed to pass and which will be blocked or refused. In some large organizations, you may even find a firewall located inside their corporate network to segregate sensitive areas of the organization from other employees. Many cases of computer crime occur from within an organization, not just from outside.
Firewalls can be constructed in quite a variety of ways. The most sophisticated arrangement involves a number of separate machines and is known as a perimeter network. Two machines act as "filters" called chokes to allow only certain types of network traffic to pass, and between these chokes reside network servers such as a mail gateway or a World Wide Web proxy server. This configuration can be very safe and easily allows quite a great range of control over who can connect both from the inside to the outside, and from the outside to the inside. This sort of configuration might be used by large organizations.
Typically though, firewalls are single machines that serve all of these functions. These are a little less secure, because if there is some weakness in the firewall machine itself that allows people to gain access to it, the whole network security has been breached. Nevertheless, these types of firewalls are cheaper and easier to manage than the more sophisticated arrangement just described. Next figure illustrates the two most common firewall configurations.
[image obtained from "http://tldp.org/LDP/nag2/lag2_0901.jpg"]
Access Control
Control access to data is fundamental for security purposes of computing systems. Access rights are a useful technique to control access that a user may have for see, manipulate or modify some data or information.
Most common access rights are:
- Reading access.
- Writing access.
- Execution access.
One way to implement this, is by an access control matrix with the following parameters:
- Rows for users.
- Columnsfor data.
- Cell for access rights a user has to use an object.
[image obtained from: "https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhTxcYjlxHh4JbAp4Z0B73-Xfx_c1xKs30NkZ6O3XPNUCD69BfVEC9xw9KMhBslhyJ85lv66ond0T78xlmB0JZb_EVpQT-CfcF46VJe7hmr1UpiYTTLVu1OCSPYyWH2rva4xIj7DSx57eM/s1600/sp.jpg"]
References:
http://librosnetworking.blogspot.com/2009/10/protocolos-de-encriptacion.html
http://exa.unne.edu.ar/depar/areas/informatica/SistemasOperativos/SO14.htm
http://tldp.org/LDP/nag2/x-087-2-firewall.introduction.html